Social engineering has become the way of life for hackers. And honestly, they don’t even try the most obvious routes any more. I get messages like the ones below on a relatively regular basis these days and I want to talk about it. Because it’s rarely legit…
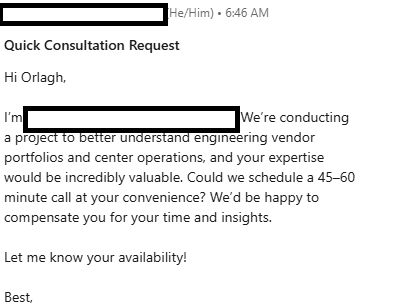
What raised my suspicions?
Well, first off, they were happy to compensate me for my thoughts on engineering vendors. Seriously, major red flag. Most of us don’t have insights that deep and frankly, most academic research institutions are running on shoestrings. So offering money/ compensation was a major deal. It means it’s market research.
Second, the man who contacted me, and I’m not going to name and shame, has been with the organisation for less than a month.
Third, I’m well aware that while many of these conversations are benign, the information I could give out to various outsiders about my role and the decision making processes within my organisation could be severely detrimental to my organisation in the marketplace.
(At this point, if any of my IT security people are reading this, they’re probably cheering! Yes, something did sink in from all those training sessions…)
And the truth is – I’m not even that senior in my organisation.
Confidentiality agreements
Most employers (in Ireland anyway) have some sort of confidentiality agreements with their employees. It might not be too onerous, since most of us have very little access to any sort of secure information, but you’d be amazed at what counts as “insider trading“.
It’s really easy, in the context of a consultation like the one above, to be flattered into revealing more than you planned. You know, you’re chatting away, you’re building rapport with the person interviewing you, they’ve identified you as an expert in your field (which let’s face it, you are!) It can be easy to let things slip.
I mean, they’re designed that way.
Now, you might be thinking you know nothing about anything worth worrying about in your position. That you’re too low on the totem pole to be concerned about anything you say to anyone – not true. Why do you think they’re targeting you? So, be careful here.
Random things to be aware of
I know from working in facilities for years, that very often, those teams are aware of VIP visits long before most other departments. Now for a lot of us in these departments, a VIP visit is a pain in the… neck… of extra work, random spend requests, budgets going out the window, and general chaos around what bathroom will the VIP be using or how do we manage to make them look accessible to the employees while keeping them safe from acts of sabotage, or worse – awkward questions!
(OK the keeping them safe is mostly about keeping them on the path they’re meant to be on and not wandering off into the most dangerous section of the factory with limited PPE… senior management can be similar to toddlers in many ways)
But those VIP visits are rarely for nothing. It’s usually a sign that something is going really, really well or really, really badly in the site. And while that information is possible commonly known within the organisation, you’d be amazed how little escapes into the general marketplace sometimes.
Random requests
The “engineering vendor portfolio” bit was what really tipped me off above. Portfolio? That’s rarely used in engineering. Architecture, sure. Project management? Yeah. Engineering? Maintenance? High unlikely. And the only reason I’m not saying “never” is because someone, somewhere will “well, acshually…” me in a heartbeat.
Now, there are requests I do respond to – willingly and happily. Students looking for information on careers. Academic researchers looking for practitioners to either complete a survey or give opinions on the practicality of something they’re suggesting. But those usually come with “You don’t know me but my teacher/ lecturer Mrs X suggested you might be able to help me”. And really – Mrs X usually contacts me separately to say, here so-and-so might give you a shout, be nice to them.
(Teachers & lecturers are always either “Mrs” or “first name”. I don’t know why this is, it has nothing to do with actual marital status, it’s just a thing. And the younger the student, the more true this rule is!)
So, if you’re a student looking to see if engineering is for you – drop me an email. I’ll answer as best you can. If you’re writing a paper based on real world maintenance/reliability, fire ahead. If you think I can help with your career, drop me a line, we’ll see what we can do.
It’s about protection
Seriously. Your own protection. Those NDAs we all sign almost as de rigour onboarding now, they’re legally enforceable. Most of us don’t need to worry about them unnecessarily, it’s not a big deal, but there are places that can help you cross a line without you even realising it.
So, pay attention to those ego-boosting messages. Question the reasons they want this information from you. Question what they will be looking for. You might look into the organisation and decide it doesn’t cross any lines – I’m delighted for you in that case. Really and truly, I am. It’s wonderful to get a bit of extra cash every now and again.
But make sure you do your research. Make sure it’s legit. Make sure you’re kept safe.
Make sure it doesn’t violate any non-compete clauses etc.
Look after yourself!

Leave a comment